Requirements:
1. Public Network
2. LAN Network
3. Linux Server (Required 3 NIC PORT)
4. Shorewall Package (Download Latest Shorewall Package and Install)
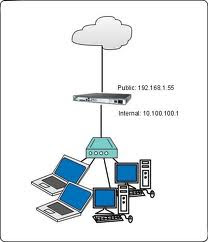
Here My Office Concepts:
I have configured Router by using Shorewall 3rd Party Tools,
Example:
ISP: 10.10.10.10 (Public)
LAN1: 172.16.4.1 - 172.16.4.254
LAN2: 192.168.4.1 - 192.168.4.10 (Public)
Scenario:
From ISP we have got one lease line (10.10.10.10) with 10 IP's Free, if we route to main lease IP then only we can use remaining 10 IP's as public IP anywhere in network, So here total now becanme 3 Network's 1. Main Public Network 2. Depended Public Network 3. Local Area Network, This 3 network also need to access ping each other network...
===================================================================
Installation:
[root@router home]# rpm -ivh shorewall-4.4.7-1.noarch.rpm
Preparing... ########################################### [100%]
1:shorewall ########################################### [100%]
[root@router home]#
Sysctl.conf File Modification: IP Forwarding
[root@router etc]# cp sysctl.conf sysctl.conf.org
[root@router etc]# vi sysctl.conf
# Controls IP packet forwarding
net.ipv4.ip_forward = 1
(default it was 0 make it 1)
Basic Network & IP OF NETWORKS:
1. Public: 10.10.10.10 net eth0
2. Public + Private: 192.168.4.1 dmz eth2
3. Local: 172.16.4.1 loc eth1
Host Name
[root@router ~]# cat /etc/sysconfig/network
NETWORKING=yes
NETWORKING_IPV6=yes
HOSTNAME=edurouter.xyz.com
Put ISP DNS in resolv.conf file[root@router ~]# cat /etc/resolv.conf
; generated by /sbin/dhclient-script
#search localdomain
nameserver IPS DNS IP
nameserver IPS DNS IP
[root@router ~]#
Setup IP
[root@router ~]# ifconfig
eth0 Link encap:Ethernet HWaddr XX:XX:XX:XX:XX
inet addr:10.10.10.10 Bcast:xx.xx.xx.xx Mask:255.255.255.0
inet6 addr: fa80::x11:58ff:feyc:5fa7/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:111447029 errors:0 dropped:0 overruns:0 frame:0
TX packets:99925403 errors:0 dropped:0 overruns:0 carrier:0
collisions:573853 txqueuelen:1000
RX bytes:4184601542 (3.8 GiB) TX bytes:1685430657 (1.5 GiB)
Interrupt:193 Base address:0x2400
eth1 Link encap:Ethernet HWaddr XX:XX:XX:XX:XX
inet addr:172.16.4.1 Bcast:172.16.4.255 Mask:255.255.255.0
inet6 addr: fe81::2z0:9llff:fe14322:7979/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:3227980 errors:0 dropped:0 overruns:0 frame:0
TX packets:17165972 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:323716456 (308.7 MiB) TX bytes:669689826 (638.6 MiB)
Base address:0xecc0 Memory:fe100000-fe120000
eth2 Link encap:Ethernet HWaddr XX:XX:XX:XX:XX
inet addr:192.168.4.1 Bcast:192.168.4.255 Mask:255.255.255.0
inet6 addr: f3e80::2a1fg0:7bff:fe4bs:b47/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:106119080 errors:0 dropped:0 overruns:0 frame:0
TX packets:94155429 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:2329561954 (2.1 GiB) TX bytes:3487500317 (3.2 GiB)
Interrupt:201 Base address:0x4000
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:2934 errors:0 dropped:0 overruns:0 frame:0
TX packets:2934 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:11665575 (11.1 MiB) TX bytes:11665575 (11.1 MiB)
[root@router ~]#
Configuration of Shorewall files: (Before modifiying take original file backup for your safety purpose)
Zone File (Introduce your Zone with IP Version)
[root@router etc]# cd /etc/shorewall[root@router shorewall]# cp zones zones.org
[root@router shorewall]# vi zones
###############################################################################
#ZONE TYPE OPTIONS IN OUT
# OPTIONS OPTIONS
fw firewall
net ipv4
loc ipv4
dmz ipv4
[root@router shorewall]#
==========================================================================================================================interfaces Interfaces File (Introduce your zones to Ethernet)
[root@router shorewall]# cp interfaces interfaces.org
[root@router shorewall]# vi interfaces
###############################################################################
#ZONE INTERFACE BROADCAST OPTIONS
net eth3 detect routeback
loc eth1 detect tcpflags,routeback
net eth2 detect tcpflags,routeback
~
===========================================================================================================================
Policy File (Give Permissions to zones to accepts each other)
[root@router shorewall]# cp policy policy.org
[root@router shorewall]# vi policy
loc dmz ACCEPT
loc fw ACCEPT
fw loc ACCEPT
fw dmz ACCEPT
#dmz loc ACCEPT
# If you want open access to the Internet from your Firewall
# remove the comment from the following line.
fw net ACCEPT
net all DROP info
# THE FOLLOWING POLICY MUST BE LAST
all all REJECT info
============================================================================================================================
Masq
[root@router shorewall]# cp masq masq.org
[root@router shorewall]# vi masq
###############################################################################
#INTERFACE SOURCE ADDRESS PROTO PORT(S) IPSEC MARK USER/
# GROUP
eth3 eth1
eth2 eth1
==============================================================================================================================
Rules (Give your own company rules, open port for your required services)
[root@router shorewall]# cp rules rules.org
[root@router shorewall]# vi rules
# Accept DNS connections from the firewall to the Internet
#
ACCEPT fw net tcp 53
ACCEPT fw net udp 53
#
#
# Accept SSH connections from the local network to the firewall and DMZ
#
ACCEPT loc fw tcp 22
ACCEPT loc dmz tcp 22
#
# DMZ DNS access to the Internet
#
ACCEPT dmz net tcp 53
ACCEPT dmz net udp 53
ACCEPT loc net tcp 53
ACCEPT loc net udp 53
ACCEPT loc fw tcp 53
ACCEPT loc fw udp 53
ACCEPT dmz fw tcp 53
ACCEPT dmz fw udp 53
ACCEPT loc net udp 123
ACCEPT loc fw udp 4242 # Ntop
#
# Make ping work bi-directionally between the dmz, net, Firewall and local zone
# (assumes that the loc-> net policy is ACCEPT).
#
ACCEPT net fw icmp 8
ACCEPT loc fw icmp 8
ACCEPT dmz fw icmp 8
ACCEPT loc dmz icmp 8
#
#ACCEPT vpn dmz icmp 8
#ACCEPT dmz vpn icmp 8
#
ACCEPT dmz loc icmp 8
ACCEPT dmz net icmp 8
ACCEPT fw net icmp
ACCEPT fw loc icmp
ACCEPT fw dmz icmp
ACCEPT net dmz icmp 8 # Only with Proxy ARP and
ACCEPT net loc icmp 8 # static NAT
ACCEPT loc net icmp
# additional rules (Router: July 14, 2012)
ACCEPT loc net tcp
#
# DMZ to net access rules
#
ACCEPT loc fw tcp
#
# remote Desktop
ACCEPT fw net tcp 3389
ACCEPT net loc tcp 3389
ACCEPT net dmz tcp 3389
ACCEPT loc dmz tcp 3389
ACCEPT dmz loc tcp 3389
#FTP
ACCEPT net fw tcp 21
ACCEPT net fw udp 21
ACCEPT net fw tcp 20
ACCEPT net fw udp 20
ACCEPT net loc tcp 21
ACCEPT net loc udp 21
ACCEPT net loc tcp 20
ACCEPT net loc udp 20
======================================================================================================================================
Shorewall.conf file (Check your config file should like below)
[root@router shorewall]# cp shorewall.conf shorewall.conf.org
[root@router shorewall]# vi shorewall.conf
# S T A R T U P E N A B L E D
###############################################################################
STARTUP_ENABLED=Yes ------------------------> Default is no, make it yes
###############################################################################
# V E R B O S I T Y
###############################################################################
VERBOSITY=0 -------------------------------------> Default is 1, make it 0
###############################################################################
# L O G G I N G
###############################################################################
LOGFILE=/var/log/messages
STARTUP_LOG=/var/log/shorewall-init.log
LOG_VERBOSITY=1 ------------------------> Default is 2, Make it 1
LOGFORMAT="Shorewall:%s:%s:"
LOGTAGONLY=No
LOGRATE=
LOGBURST=
LOGALLNEW=
BLACKLIST_LOGLEVEL=
MACLIST_LOG_LEVEL=info
TCP_FLAGS_LOG_LEVEL=info
SMURF_LOG_LEVEL=info
LOG_MARTIANS=No ----------------------------> Default is Yes, Make it No
======================================================================================================================================
Keep Always On Shorewall Service:
[root@router shorewall]# chkconfig shorewall --levels 235 on
[root@router shorewall]#
Start Shorewall Service:
[root@router shorewall]# service shorewall start
Starting shorewall: [ OK ] [root@router shorewall]#
Now try to ping each other from all 3 networks....
Thanks and Regards,
Sandeep CC